how can check handshake password length
Check Nyambaa solution here Rohan Khude. As you can notice the backend server did not get any Certificate from the Client Certificate Length.
TLS handshake failed google suggested solutions not helping and tried to switch from the default UDP to TCP but that only caused the client to repeatedly report that the connection timed out.
. Ssh_handshake_attempts int - The number of handshakes to attempt with SSH once it can connect. Check the maximum length of columns and index keys. If there are figures on that line you can go back.
EAP-Microsoft Challenge Handshake Authentication Protocol version 2 MS-CHAP v2 Secure password EAP-MS-CHAP v2 is an EAP type that can be used with PEAP for password-based network authentication. Ssh_bastion_port int - The port of the bastion host. The write stream for put.
If your server has a strong preference for this cipher or use only this cipher this can trigger a. It used to work in Ubuntu 1604. The SSLTLS Handshake Process in TLS 12 vs TLS 13.
See key managertrust manager. Below figure shows the steps involved in 4-Way handshake process. Crack password using hashcat.
This attack forces AP-connected computers to drop their connections and reconnect with the hackers soft AP disconnects the user from the modem so they have to connect again using their password which one can extract from the. EAP-MsCHAP v2 can also be used as a standalone method for VPN but only as a PEAP inner method for wireless. Ssh_bastion_host string - A bastion host to use for the actual SSH connection.
Sudo apt install hashcat. We all know that scoring superbly on internal assessments is a great way to boost our IB grades. But how do we get started on a lab report and crucially.
Certfile keyfile None password None Load a private key and the corresponding certificate. TLS 12 uses a handshake that makes multiple roundtrips between the client and the server. Lets now look at the Message 9 to check the contents of the certificate sent by the Message Processor.
When you are capturing your data analyze the problem you will get the three-way handshake. Check your domain or IP address against 10 popular blacklist databases and ensure that they are not blacklistedNeed not worry if your resources are in the list Site24x7 can help you remove your resources from the blacklist. 25 IB Chemistry IA Topic Ideas.
How many handshakes. RAND_status can be used to check the status of the PRNG and RAND_add. A named collection of state information including authenticated peer identity cipher suite and key agreement secrets that are negotiated through a secure socket handshake and that can be shared among multiple secure socket instances.
Dictionarytxt - word list suppose wpacrackhccapx is the handshake file. Most Popular Quick Fix. These cipher suites can still be enabled by SSLEnginesetEnabledCipherSuites and SSLSocketsetEnabledCipherSuites methods.
Check is everything oky. Well get into what that means specifically in a. If its a prv discharge then it stays open and visible.
For example every machine on the internet be it laptops or your web servers have a unique IP address. The next step is to add a secret key to the hash so that only someone who knows the key can use the hash to validate a password. Here is the details about each step.
For example if one side dont like to talk with an specific TLS version or because of an certificate-problem. This means that setting autoClose. Hence the backend server sends the Fatal Alert.
Request your 202108 declaration on the declaration screen. As with the TLS 12 handshake a Client Hello message starts the handshake off but this time it comes packaged with a lot more information. Hashcat -I to use hashcat you need gpu.
No more eventual retransmissions of EAPOL frames which can lead to uncrackable results No more eventual invalid passwords sent by the regular user. No more waiting for a complete 4-way handshake between the regular user and the AP. If its from the condensate system then it needs correctly discharging to a drain.
MyDebug function - Set this to a function that receives a single string argument to get detailed local debug information. Blacklist Check for IP Address Domain Email. An unexpected TLS packet was received.
Therefore it is smaller in terms of characters because the maximum length of a character is now four bytes instead. TLS 13 has reduced the number of supported ciphers from 37 to 5. Cant see a period in the View Edit Employees dropdown.
This can be accomplished two ways. This message will also appear if the TLS handshake stops for different reasons. It contains good options like the TCP options.
Tried that before but only my answer works Rock. When I test the setup on one of my Linux virtual machine clients I get the error. No more lost EAPOL frames when the regular user or the AP is too far away from the attacker.
Passwords should be at least 8 characters in length and use a mixture of upper and lower case letters numbers and symbols. This defaults to 10. As a result the SSL Handshake failed and the connection will be closed.
They will check the boiler and work out the max equivalent flue length permissable for that model of Vaillant and also advise you on the outlet pipe at floor level. See JDK-8077109 not public. The keyfile string if.
You can filter EAPOL-Key messages using eapolkeydestype 2 wireshark display filter. 20000 integer How long in ms to wait for the SSH handshake strictVendor. 22 Oct 2021 at 1853 8.
Currently there are two different versions of the TLS handshake in use. This was actually the result of a hacked password. There is a little delay between SYN and SYN- ACK packet at.
If there are no figures in that line the file imported was not for the 202108 period. This CWNP video explain well this process have a look on it before go into details. Works for me on Debian 10.
So when you enter a domain name for. Using passwords that cant be easily guessed and protecting your passwords by not sharing them or writing them down can help to prevent this. False can no longer be supported.
Aug 21 2018 at 2248. Aug 20 2018 at 711 Rohan Khude please read the question again. When it opens check on the bottom part of your last page for the certificates total.
EAP-Tunneled Transport Layer Security. One type of man-in-the-middle attack relies on security faults in challenge and handshake protocols to execute a de-authentication attack. The certfile string must be the path to a single file in PEM format containing the certificate as well as any number of CA certificates needed to establish the certificates authenticity.
Hashcat -m 2500 wpacrackhccapx dictionarytxt. Example bruteforce for length 8 password using 0. From this you can determine the shift time and figure out if you have captured packets on the client-side or the server-side.
When converting from utf8 to utf8mb4 the maximum length of a column or index key is unchanged in terms of bytes. Commonly known as phonebook of the internet DNS translates domain names to IP addresses so browsers can retrieve the necessary information. This is probably the most tedious part of the whole upgrading process.
True boolean - Performs a strict server vendor check debug. Check DNS report A ALL MX NS analyze with our DNS checker for free. An TLS handshake timeout mostly does not mean the internet connection is to slow.
As you can see the TLS 13 handshake is significantly shorter than its predecessors. TLS 12 and TLS 13. No more fixing of nonce and.
As long as an attacker can use a hash to check whether a password guess is right or wrong they can run a dictionary or brute-force attack on the hash. Check out our tutoring packages to help you smash your IA. Unable to access git.
I quickly read OpenVPN on OpenVZ TLS Error.

Configuring The Vlans That Are Allowed To Access The Router Networking Router Segmentation
Dragonfly Handshake Diagram Download Scientific Diagram
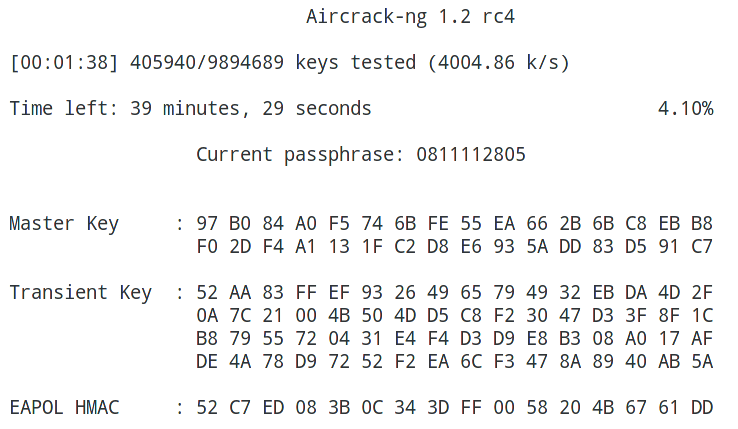
Hacking Wpa Wpa2 Passwords With Aircrack Ng Hashcat Kalitut
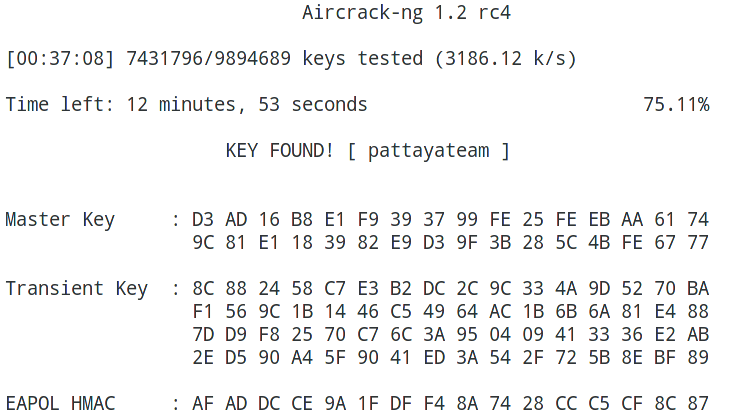
Hacking Wpa Wpa2 Passwords With Aircrack Ng Hashcat Kalitut
A Detailed Diagram Of The Four Way Handshake Msg Message Download Scientific Diagram
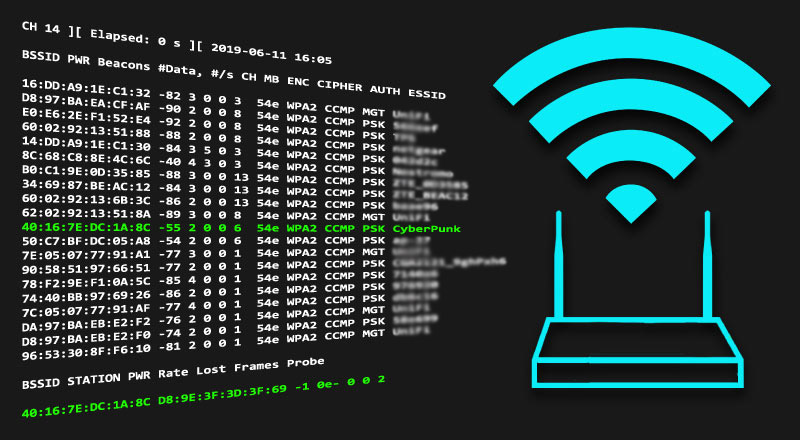
Capturing Wpa Wpa2 Handshake Cracking Principles Cyberpunk
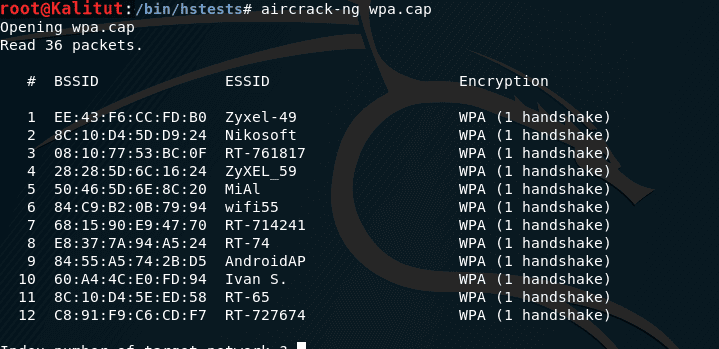
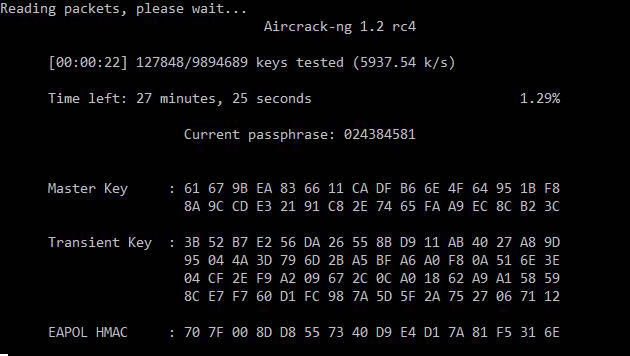
How To Extract Handshake From Capture File With Multiple Handshakes Kalitut

Hacking Wpa Wpa2 Passwords With Aircrack Ng Hashcat Kalitut
Log In As An Alum Set Your Handshake Password Handshake Help Center
0 Response to "how can check handshake password length"
Post a Comment